Developers deal with implementing authentication and authorization on a daily basis at work. And they ought to design a system that offers the optimum user experience. Users had to create a username and password, enter their email address, and other onerous steps in the past. Now that third-party firms like Google, Facebook, Twitter, etc. frequently handle this function, everything is really simple: you just pick your preferred social network and log in using their assistance. Very simple, right? Yes, if you're just a user, but if you want to create applications, you need to figure out the best way to include authentication into your project.
For these uses, I advise adopting Auth0 because it is a practical and profitable solution. Spend a moment reading my article if you are not ready to accept my word for it. I'll try to convince you and lay out all the information about Auth0 and Authentication.
Authentication vs. Authorization
Let's first define "authentication" and "authorization" and examine how they differ from one another. After all, you should know what is what, so to speak, and get the hang of things if you want to find the ideal approach to implement modern authentication and authorization systems.
Actually, the purpose of authentication is to confirm your identity. You authenticate when you enter your name and password to access the application. In contrast, authorization verifies your access to a certain resource, it may be a collection of permits to carry out specified actions.

Problem with Authentication and Authorization
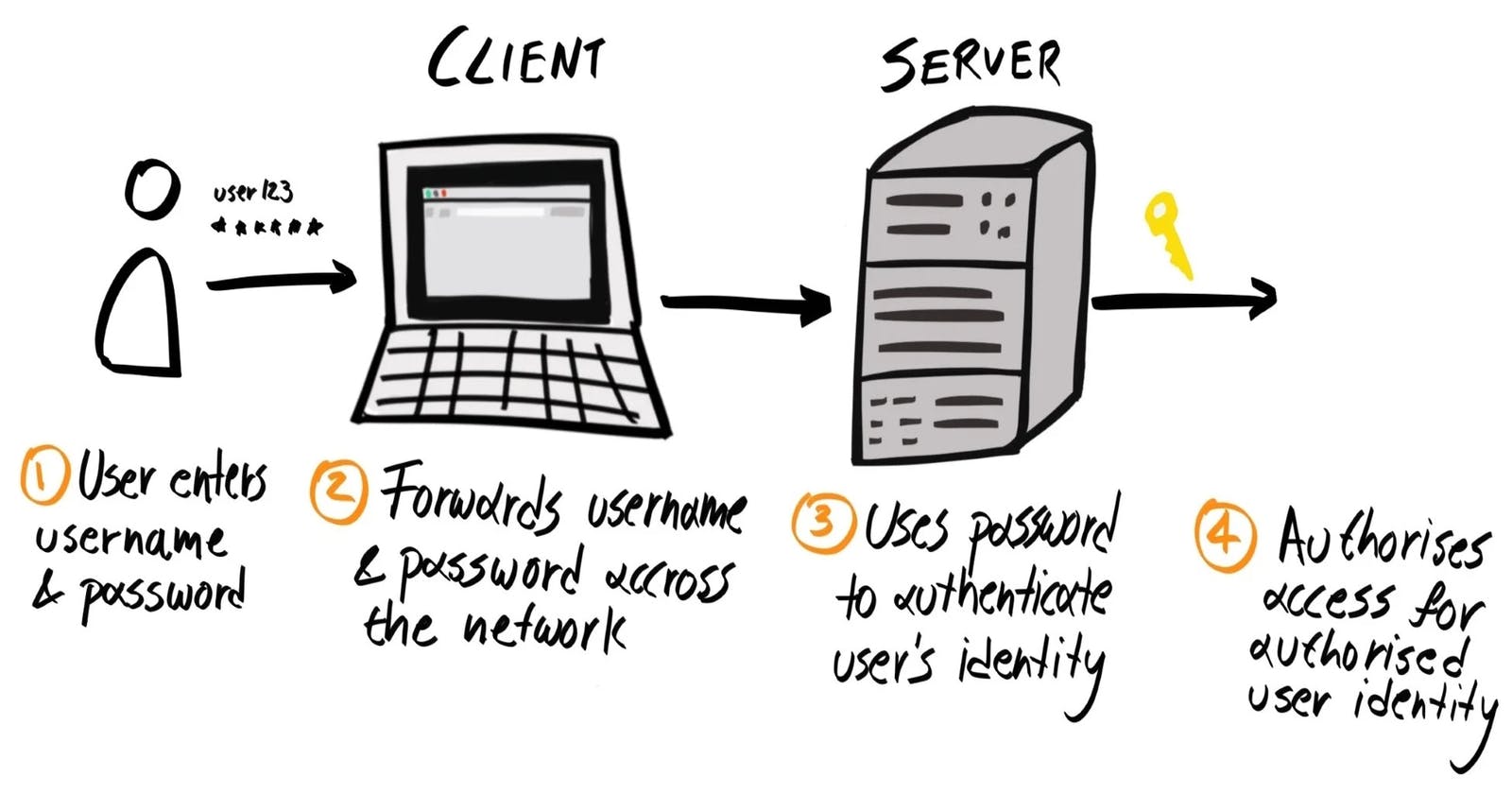
Everyone is aware of how the application's normal authentication works: the user inputs his email address, password, etc. Following that, these data are compared to those that have already been preserved. The user is given access when the data match.
Thankfully, there are now a tone of additional techniques with up-to-date authentication capabilities.
We will only take into account the most essential and relevant methods of implementing authentication. Why, in the end, reproduce what has already been made irrelevant ?
Session-Cookie Based Authentication
Here, we have cookies (or sessions), which are where we will store user information.
Because the cookie containing the authentication record is saved on the user's side, cookie-based authentication is different from the session in that there is no risk of overtaxing the server. Unfortunately, the session does not provide this benefit because the cookie only includes a unique identifier for accessing the authorization data (which the server has in a special unique file).
Cookies are viewed as being less trustworthy (they can be stolen, and an attacker will have access to personal data). On the other hand, because the session based authentication is relatively brief and the data file is kept on the server, it may get overloaded as the project grows.
The Single Sign On (SSO) technique is also used, but this time with cookie-based authentication. If a business with multiple services wishes to add authentication and considerably streamline the process, the SSO technique is particularly helpful.
Google, with its Gmail and YouTube services, is a good example. The user has immediate access to all of the company's services because of Google Accounts, a strong coordination hub. The verification data is stored in the cookies, which are used for this reason.
Token based Authentication
Do you wish to stay away from the mentioned overloading as well as the other issues listed above? The usage of tokens, which are brief pointers to the website or application you need, is then a good alternative. This pointer is proof that the user is authorised to access the relevant resource and was obtained with the assistance of the authentication service (if the authorization data turned out to be correct).
We won't dive into all the specifics, but suffice it to say that the token-based approach enables you to extend and improve the website (application) without overloading the server with data.
JWT based Authentication is the best example

Social Network Authentication
Right now, we're referring to social login or social sign-in. Formally, Social Authentication is a type of SSO approach that accelerates the registration/login procedure for your application.
If they have an account on one of the social networks, users can access your application with a single tap, considerably enhancing the user experience. Additionally, social networks have already taken care of the security of user data and the need to validate email addresses, so developers do not need to worry about these issues.

Multi-factor authentication
Before discussing how to construct a modern authentication service, it is important to bring up multi-factor authentication, which increases access security by utilizing multiple ways to confirm the user's identity.
Examples of multi-factor authentication include Facebook, Google, and other well-known websites. A user must first log in and enter a password before receiving an email with a one-time password (or verification code) (or SMS).
Maximum data security requires the use of such an algorithm. Social network authentication is sufficient in the majority of situations.

What is Auth0?
A safe and universal service called Auth0 makes sure that authentication and authorization are functional. It operates on the basis of the tokens we've discussed and makes use of several identity providers. Social networks are among the platforms it works with. So, if you want to integrate social authentication into apps, the solution works perfectly.
Additionally, developers are happy with the options offered: They may utilise Safari as an application that manages user accounts and the login process in addition to native SDK social services. You can employ specialized security software features depending on the operating system browser to stop identity theft.
Why Auth0 is a Right Solution ?
There are numerous social networks, including Twitter, Facebook, and Google. Additionally, each of these services has its own system for verification and identification.
You should look for handy options that will streamline the entire procedure to avoid the need to implement authentication for each choice separately.
In order to accomplish this, the start-up Auth0 was established.
From a functional standpoint, Auth0 takes care of both the issuing of access tokens (JWTs) that may be used by your own APIs as well as the authentication provided by Facebook and other social providers.
Additionally, it would probably compel you to align your implementation with current authentication and authorization standards (OpenID Connect and OAuth2). This would be advantageous from a security standpoint because those specifications have undergone security evaluations made by several parties and have also been put to the test in real-world scenarios. On the other side, a custom implementation might work, but it's simple to miss crucial features. As a result, implementing using Auth0 and standards may even be more difficult than doing it in a custom way, but it will likely be more secure.
The perk of using Auth0
Custom UI Design
With Auth0, you can choose between a built-in UI and a custom UI. This means that you can decide whether an application should use the browser-based login flow or the native login flow. And all it takes to modify it is a simple setting adjustment on the Auth0 site.
The UI of the universal login pages can also be modified. The pages can be made uniquely yours by adding your own color's, phrases, logos, and translations.
Analytics
There are several tools available that you may utilize, in addition to the technical aspects, to assess the traffic to your website from an authentication perspective. As this is crucial for a startup, and it's difficult to incorporate this feature on your own into a product or SaaS.
For instance, it might give you the information below:
Amount of current users
A particular application is filtered according on new user login activity on the application.
Login activities

Attack Protection
You may set up the most popular defense to shield users from automated attacks like bot detection or brute force attacks in this portion of the Auth0 portal.

Conclusion
With thorough statistics, a wide range of possible providers, and a selection of user-friendly features the developer will truly like, Auth0 offers the most comprehensive capabilities to assure user authentication and authorization. In comparison Passport, Keycloak, Okta, and Centrify significantly lose in comparison.
In conclusion, you’ll need to review the pros and the cons and decide for yourself. You need to find the perfect solution (as far as possible), and the systems described are substantially inferior to Auth0.